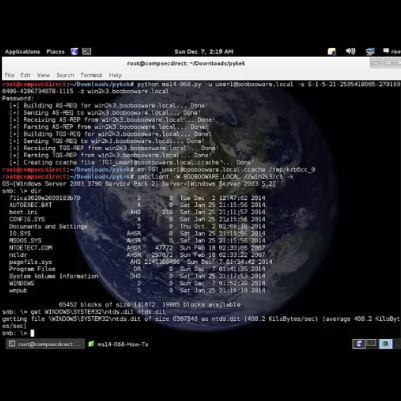
My CPAP has a recall; let’s open it instead!
"If you or a loved one has ever used a CPAP device..." Our President, Jose Fernandez, gave a medical device presentation at BioHacking Village during DefCon 31. This presentation focused on bringing awareness to privacy related issues related CPAP devices, how to passively identify some CPAP devices and follow on work for exploit related research for [...]